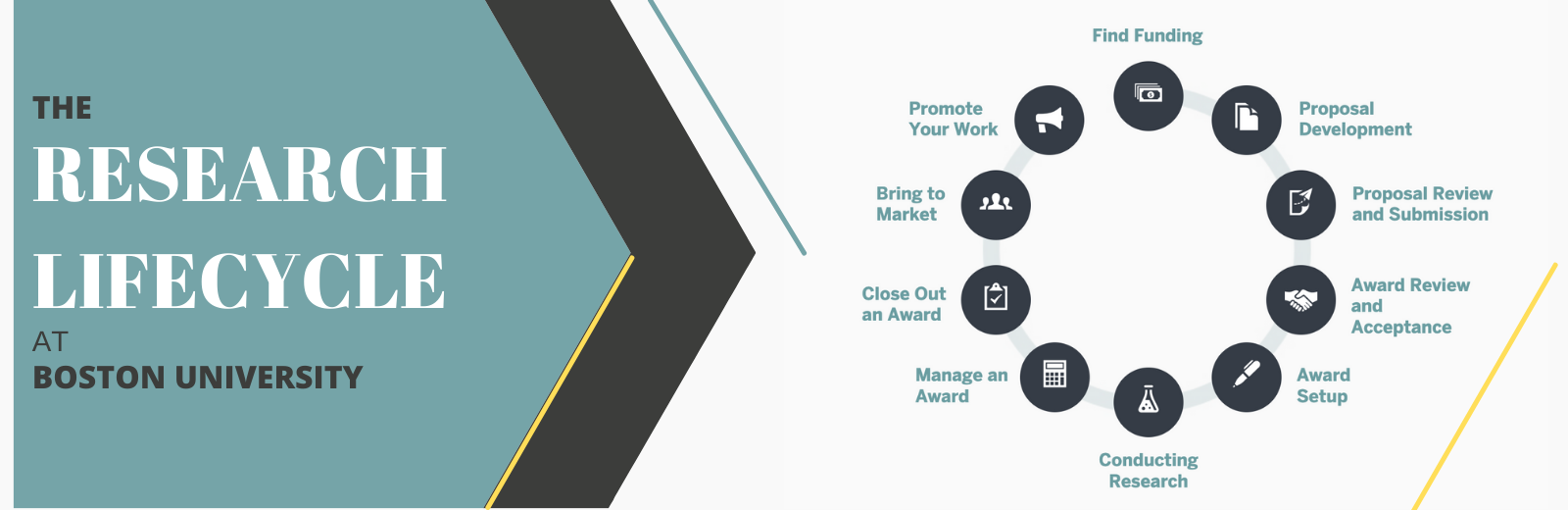
From preparing your proposal, to reviewing a Data Use Agreement and closing out your research, Information Security is here to help you throughout the research lifecycle with research security. We are typically involved in the following steps of the cycle, but are available to consult at anytime:
Award Review and Acceptance
When Office of Sponsored Programs, Industry Engagement, or other BU contracting offices review a research contract that has special security requirements, they will ask BU Information Security to conduct a review. As part of that review, we will reach out to the PI and ask about the devices and services that will be used. Our role is to ensure that researchers are using devices and services that comply with the contractual requirements. In some cases, we will work with IS&T or the applicable IT support group to add any additional security controls required by the contract.

